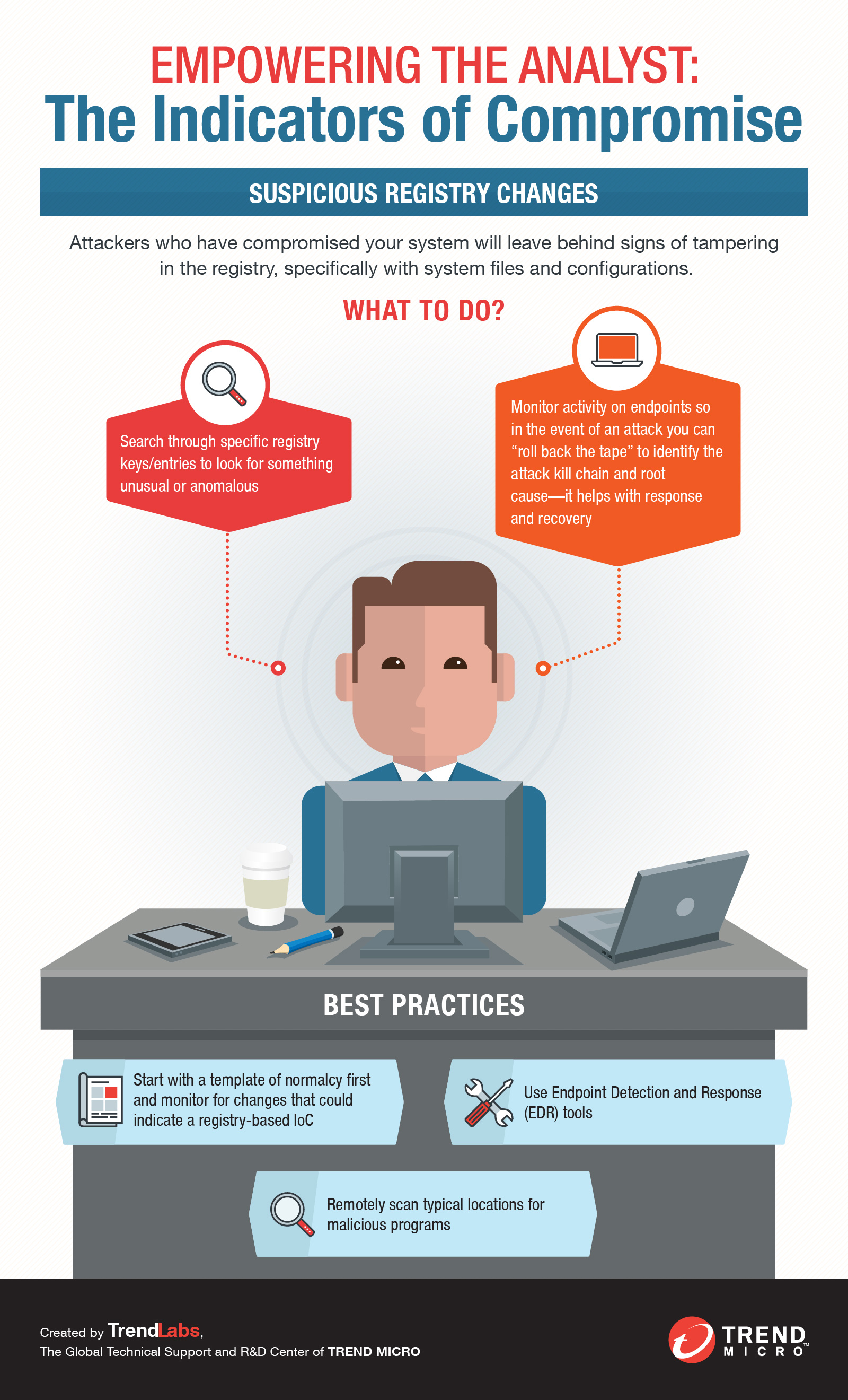
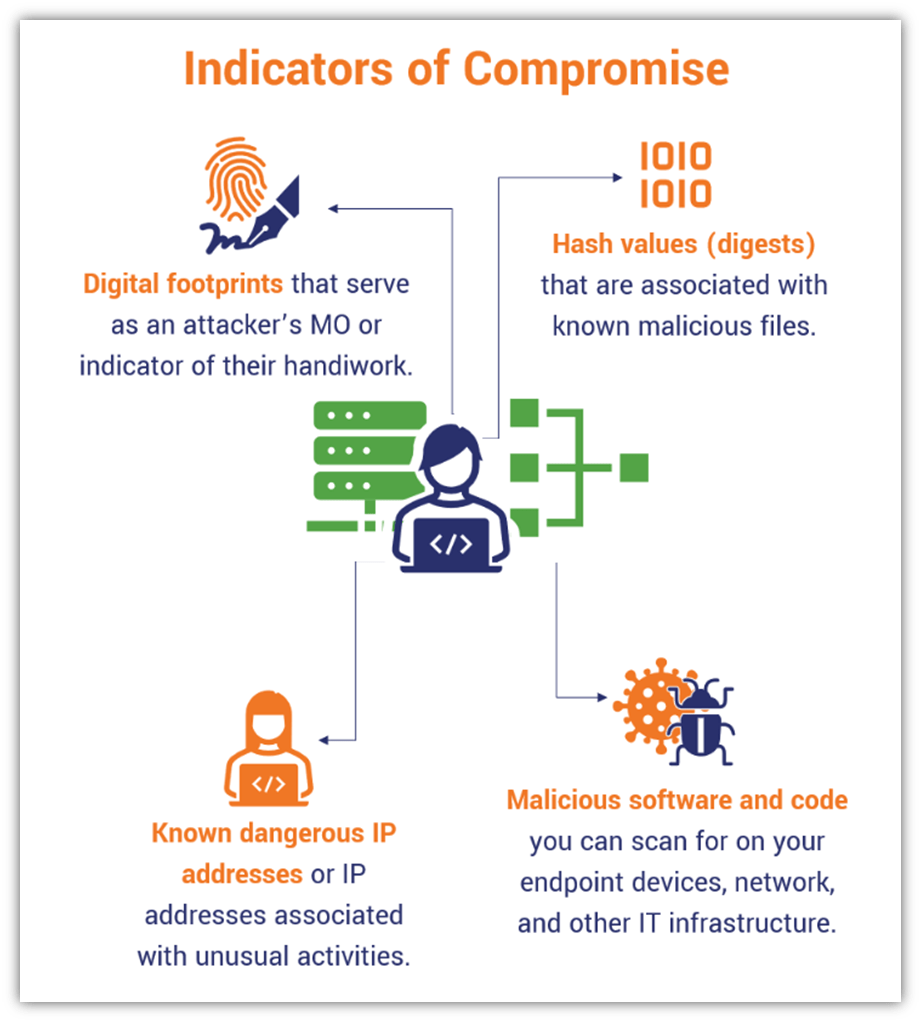
The attacker can compromise various components in a control system,... | Download Scientific Diagram
System-Integrity-is-compromised-Is-it-due-to-unlocked-bootloader - English Motorola - MOTO COMMUNITY

System hacked alert after cyber attack on taplet network. compromised information concept. internet virus cyber security and cybercrime.. 素材庫相片| Adobe Stock